Short description
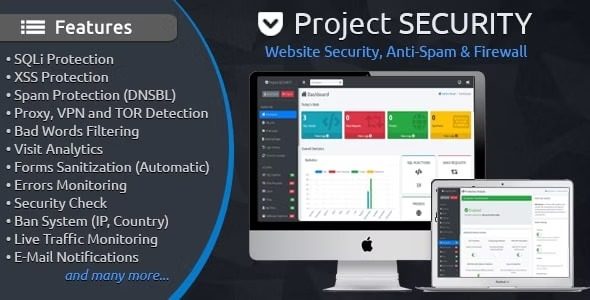
Project Security is a powerful website security tool that offers advanced measures to protect your website from various threats, including SQL injections, cross-site scripting vulnerabilities, spam, proxy servers, VPN servers, and TOR servers. It uses code recognition and patterns to automatically take action in the event of any known hacker assault or new, unknown danger. The robust admin interface allows you to examine all logs and has an integrated ban system where you can block countries, IP addresses, browsers, operating systems, referrers, and internet service providers (ISPs).
Project Security is a powerful web application firewall that can safeguard any PHP application. It runs quickly, has been fine-tuned, and uses almost no system resources. Key features include SQL Injection (SQLi) security safeguards against cross-site scripting (XSS) vulnerabilities and SQL injections, protection against proxy, VPN, and TOR users prevention from users posing as proxy servers, spam protection feature, input sanitization protection module, real-time filtering of offensive language, DNSBL Integration, intelligent pattern recognition, prohibition mechanism, anti-fake bot measures, review of headers, IP lookup tool, email notifications, informational dashboard, practical implementation resources, monitoring for errors,.htaccess manager, file whitelisting and IP address addressing, current traffic conditions, Visit Analytics, and a tool for verifying PHP settings.
Project Security is highly enhanced, completely flexible, quick to set up, and simple to operate. It requires PHP and MySQL tables, and can be installed using the Installation Wizard.
Always a step ahead of the rest!
One Membership with Unlimited Access
Here you can freely download plugins, themes, PHP scripts, Windows software, and other tools needed by webmasters for the popular platform.






















description
Project SECURITY Nulled Script
Project SECURITY – Website Security, Anti-Spam & Firewall
If you want to keep your website safe from intruders, assaults, and other dangers, install Project Security. It will make sure that your website is safe against a lot of different kinds of attacks, including SQL injections, cross-site scripting vulnerabilities, spam, proxy servers, VPN servers, TOR servers, and more.
Using code recognition and patterns, Project Security automatically takes action in the event of any known hacker assault or new, unknown danger. These algorithms are comparable to those utilized by large industrial corporations.
You can examine all logs via the robust admin interface that comes with it. It also has an integrated ban system where you may block countries, ranges of IP addresses, browsers, operating systems, referrers, and internet service providers (ISPs). Numerous options and settings are available in the admin panel. It makes managing your website’s security a breeze.
From popular shopping cart software to bespoke scripts, Project Security is a strong web application firewall that can safeguard any PHP application. Advanced and robust security measures are available to every website administrator. It runs quickly, has been fine-tuned, and uses almost no system resources.
Key Points
SQL Injection (SQLi) security safeguards against cross-site scripting (XSS) vulnerabilities and SQL injections.
Protection against Proxy, VPN, and TOR Users Prevention from users posing as proxy servers.
Protect your website from spammers and spam bots with our spam protection feature.
An input sanitization protection module is available that automatically cleans all requests and answers, both incoming and outgoing. Complete request scanning in real-time.
A module for real-time filtering of offensive language, links, phrases, and other material types.
Protect your website against malicious visitors using DNSBL Integration, which integrates with top spam databases.
Attacks and vulnerabilities that have not been discovered yet may be detected via intelligent pattern recognition.
Prohibition Mechanism
Prohibit and reroute access from certain countries, IP addresses, operating systems, browsers, ISPs, and referrers.
Eliminating malicious bots and crawlers The bandwidth of your website will be wasted by malicious bots and crawlers.
Anti-Fake Bot Measures
Identifying the legitimacy of the search engine bots that access your website.
Review of Headers
We shall inspect the response headers of every visitor and block them from accessing the website if we find any suspicious elements.
When malicious activity is identified, the auto-ban function will immediately ban the offending user.
Logs of Threats
The database keeps track of every danger and assault, so you may review them at a later time. (Only one of each.)
Extensive Records
Browser, OS, nation, state, city, user agent, location, and other pertinent information on the threat or attack may be found in the logs.
An IP lookup tool may reveal if an IP address is banned and allow you to research it further.
Reminders by Email
Whenever an attack or threat is identified, you will be notified by email.
Informational Dashboard
Website security statistics are shown on the dashboard.
Practical Implementation Resources
With this set of tools, you may edit.htaccess files, create hashes, and much more.
Monitoring for errors
A helpful tool that displays all of the website problems that have been recorded.
The.htaccess manager
There is no need to launch an external editor; you can change your.htaccess file right from the Admin Panel.
file whitelisting and IP address addressing
To prevent the program from blocking certain IP addresses and files, you may create a whitelist.
Current traffic conditions
Keep tabs on how people use your site in real time.
Use Visit Analytics to see how visitors interact with your site.
A Tool for Verifying PHP Settings
Verify that there are no security holes in the present PHP configuration.
A wealth of data and information on your web server is shown on the System Information Page.
Highly Enhanced
You won’t notice any lag in your site’s loading speed since the script is so small.
Completely Flexible
It looks great on a wide range of devices and screen sizes.
Quick to set up
You may install the app with the aid of the script since it is integrated with the Installation Wizard.
Simple to operate
The only lines of code you need to secure your website are two lines of code in the main.php file.
Things needed
The PHP
Tables in MySQL and PHP
How to Install (additional information)
Move the files to the host’s “Source” folder and then upload them using FTP.
Make a MySQL database (your web host should be able to help you with this).
For example, you may have uploaded the files to your website at this location: yourwebsite.com/security/.
Simply follow the on-screen prompts to launch the installation wizard.
php nulled scripts
php scripts
Related Products
The Best Products
FAQs
There are No Silly Questions — Ask, We’re answer
No, we do not offer auto-renewal. Users can renew their accounts manually whenever they want.
We offer a no-questions-asked, seven-day money-back guarantee. If you are not satisfied with your account within seven days, you can request a full refund, and we will return your money.
The software you download from us can be used indefinitely. However, to download future updates, you need to have an active subscription. If your subscription expires, you can still use the software, but you will need to purchase a new account to access updates.
Product Info
version
Updated Date
Released on
Developer Name
Category
There is a problem ?
Get Unlimited Access
Gain access to this product and enjoy limitless use of 10,000+ top-tier tools.










Reviews
There are no reviews yet.